* add aasf * add AASF format * credentials provider * add finding publisher * add finding publisher * add write AASF path * add testing * read config from file * update docker file * refactor * remove sample * add comments * Add comment in EKS config.yaml * Fix comment typo * Fix spelling of ASFF * Fix typo and other small code review suggestions * Limit length of Actual result field Avoids this message seen in testing: Message:Finding does not adhere to Amazon Finding Format. data.ProductFields['Actual result'] should NOT be longer than 1024 characters. * Add comment for ASFF schema * Add Security Hub documentation * go mod tidy * remove dupe lines in docs * support integration in any region * fix README link * fix README links Co-authored-by: Liz Rice <liz@lizrice.com>
2.4 KiB
Integrating kube-bench with AWS Security Hub
You can configure kube-bench with the --asff to send findings to AWS Security Hub. There are some additional steps required so that kube-bench has information and permissions to send these findings.
Enable the AWS Security Hub integration
- You will need AWS Security Hub to be enabled in your account
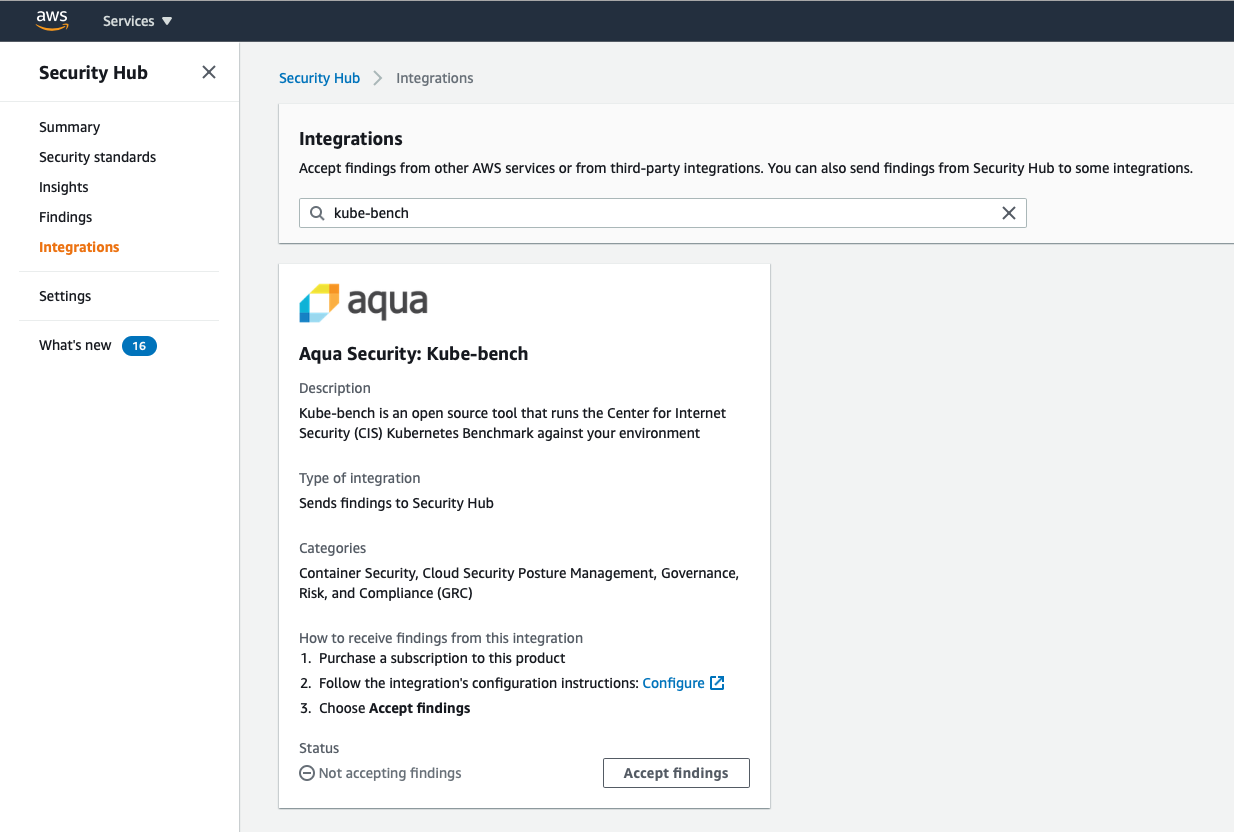
- In the Security Hub console, under Integrations, search for kube-bench
- Click on
Accept findings. This gives information about the IAM permissions required to send findings to your Security Hub account. kube-bench runs within a pod on your EKS cluster, and will need to be associated with a Role that has these permissions.
Configure permissions in an IAM Role
- Grant these permissions to the IAM Role that the kube-bench pod will be associated with. There are two potions:
- You can run the kube-bench pod under a specific service account associated with an IAM role that has these permissions to write Security Hub findings.
- Alternatively the pod can be granted permissions specified by the Role that your EKS node group uses.
Configure and rebuild kube-bench
You will need to download, build and push the kube-bench container image to your ECR repo as described in Step 3 of the EKS instructions, except that before you build the container image, you need to edit cfg/eks-1.0/config.yaml to specify the AWS account, AWS region, and the EKS Cluster ARN.
Modify the job configuration
- Modify
job-eks.yamlto specify the--asffflag, so that kube-bench writes output in ASFF format to Security Hub - Make sure that
job-eks.yamlspecifies the container image you just pushed to your ECR registry.
You can now run kube-bench as a pod in your cluster: kubectl apply -f job-eks.yaml
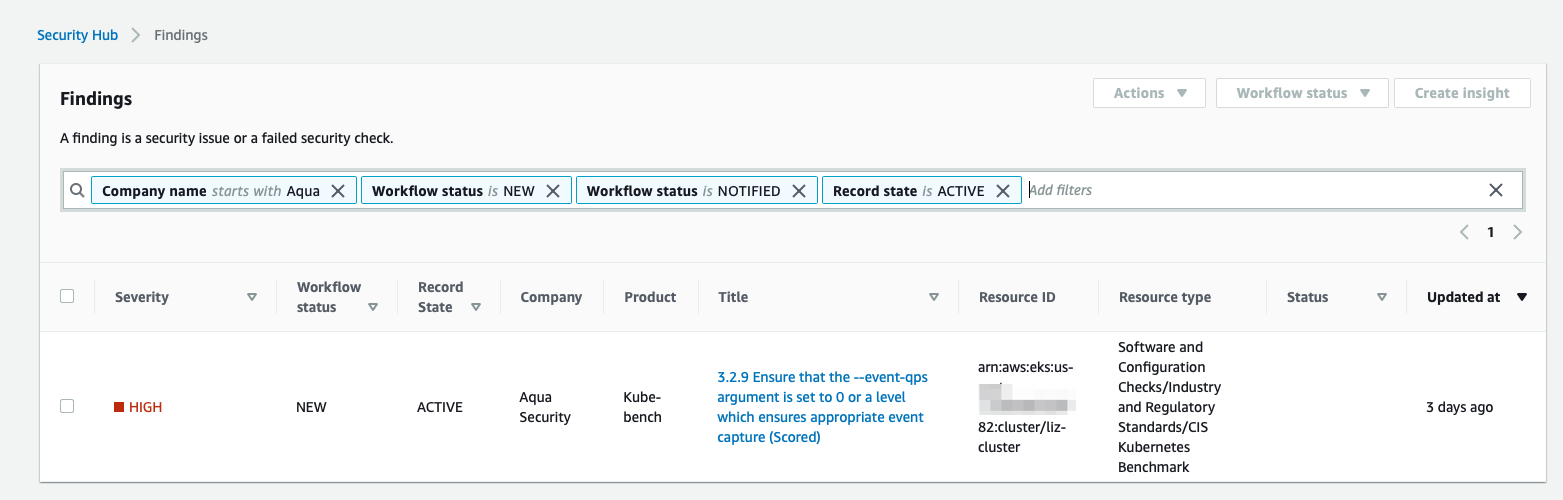
Findings will be generated for any kube-bench test that generates a [FAIL] or [WARN] output. If all tests pass, no findings will be generated. However, it's recommended that you consult the pod log output to check whether any findings were generated but could not be written to Security Hub.